With the growing number of frameworks published by MITRE, it is easy to lose track of their respective purposes and how they relate to one another. In this post, I aim to clarify the role of each framework and explain how they fit together to support modern cyber defense, incident response, and resilience.
What is MITRE?
MITRE is a not-for-profit organization that operates federally funded research and development centers (FFRDCs) and works closely with governments, critical infrastructure providers, and industry. In cybersecurity, MITRE’s role is to translate real-world attack data, operational experience, and research into open, vendor-neutral frameworks that help organizations understand threats, design defenses, and improve resilience across complex environments.
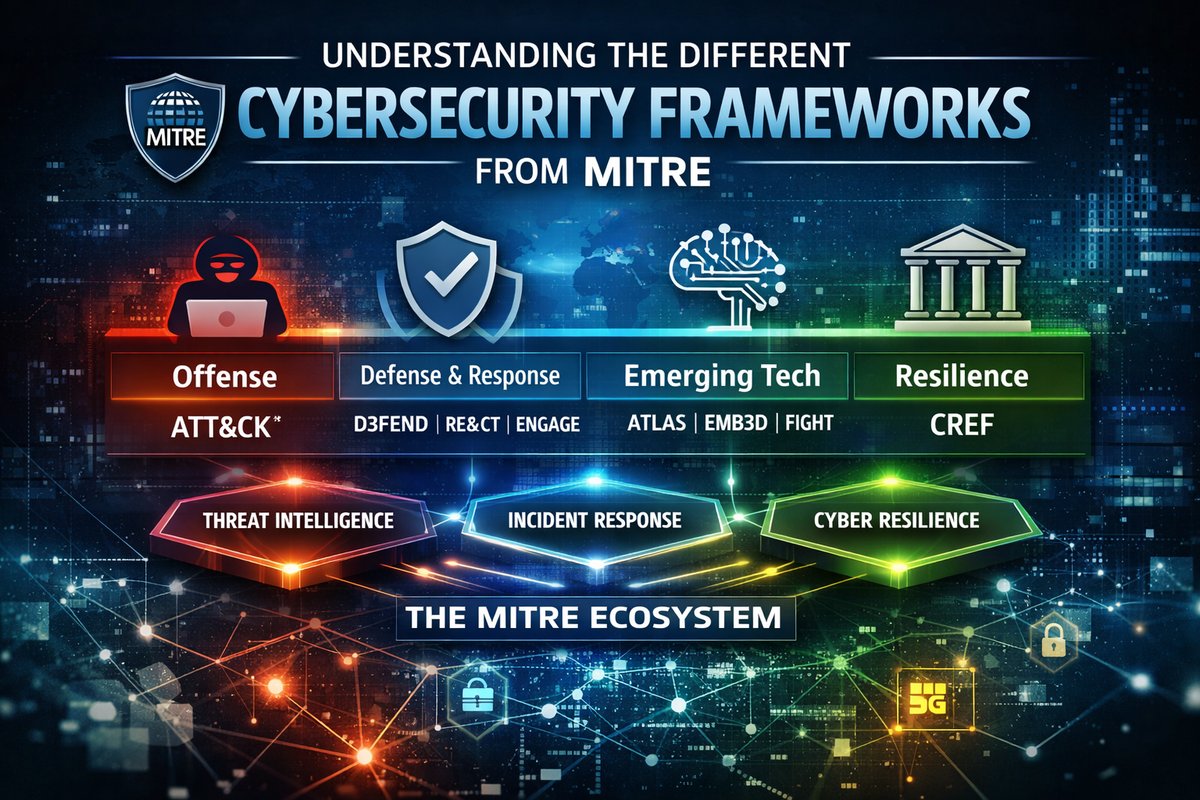
Modern cybersecurity is no longer limited to understanding attacker behavior through ATT&CK alone. Building an effective and resilient security posture requires connecting threat intelligence, defensive controls, incident response, and recovery into a coherent operating model. The MITRE ecosystem provides an interconnected set of frameworks spanning offense, defense, response, and resilience.
Below is a structured view of how these frameworks work together.
🔴 Offensive Knowledge Foundation
- ATT&CK®
The industry reference for describing adversary tactics, techniques, and procedures (TTPs) observed in real-world attacks against enterprise environments.
🔗 https://attack.mitre.org
🔵 Defensive and Response Frameworks
-
D3FEND
A knowledge graph of cybersecurity countermeasures that directly maps defensive techniques to ATT&CK-based adversary behaviors.
🔗 https://d3fend.mitre.org -
RE&CT®
An incident response–focused framework that organizes concrete response actions, enabling structured and repeatable breach handling.
🔗 https://atc-project.github.io/react-navigator/ -
ENGAGE
The evolution of MITRE Shield, centered on adversary engagement and deception, enabling defenders to control attacker movement and gather intelligence in managed environments.
🔗 https://engage.mitre.org/matrix
🧰 Specialized Domains and Emerging Technologies
-
ATLAS (Adversarial Threat Landscape for AI Systems)
Documents real-world adversary TTPs targeting AI-enabled systems—essential for organizations deploying LLMs and machine learning at scale.
🔗 https://atlas.mitre.org/matrices/ATLAS -
EMB3D
A framework dedicated to embedded device security, addressing the unique threat models of hardware and firmware across IoT, ICS, and critical infrastructure.
🔗 https://emb3d.mitre.org/ -
FiGHT (5G Hierarchy of Threats)
A specialized matrix for the 5G ecosystem, helping stakeholders understand and mitigate risks inherent to cellular infrastructure.
🔗 https://fight.mitre.org
♟️ The Strategic Layer
- CREF (Cyber Resiliency Engineering Framework)
The architectural backbone of the ecosystem. CREF defines objectives and practices that enable systems to anticipate, withstand, recover from, and adapt to adverse cyber conditions.
🔗 https://crefnavigator.mitre.org/navigator

Comments
Submit comment
No comments yet. Be the first to share your thoughts!